I recently had the misfortune of suffering a series of Malware/Trojan virus attacks on this and some other WordPress blogs we operate. I had been planning on taking measures to protect our WordPress applications from potential attacks such as this but like many other things, procrastination took first priority.
The attacks are behind us now, at least I hope (crossing fingers). And while the attacks ended up being completely unrelated to any WordPress vulnerabilities, I thought it would be beneficial to list some measures that can be put in place to help prevent “attacks” on WordPress driven blogs.
1. Robots.txt File
Use the Robots.txt file to instruct search bots and spider NOT to index certain files and directories that are part of your WordPress installation. After editing, your Robots.txt file might look something like this:
User-agent: *
Disallow: /blog/wp-
Disallow: /blog/search
Disallow: /blog/feed
Disallow: /blog/comments/feed
Disallow: /blog/*/feed/$
Disallow: /blog/*/feed/rss/$
Disallow: /blog/*/trackback/$
Disallow: /blog/*/*/feed/$
Disallow: /blog/*/*/feed/rss/$
Disallow: /blog/*/*/trackback/$
Disallow: /blog/*/*/*/feed/$
Disallow: /blog/*/*/*/feed/rss/$
Disallow: /blog/*/*/*/trackback/$
Disallow: /blog/wp-login.php
Disallow: /blog/wp-register.php
Disallow: /blog/wp-admin
Disallow: /blog/wp-includes
2. Protect wp-config.php File With .htaccess
Protect you wp-config.php file by adding the following to the .htaccess file that should reside in the root directory:
<files wp-config.php>
Order deny,allow
deny from all
</files>
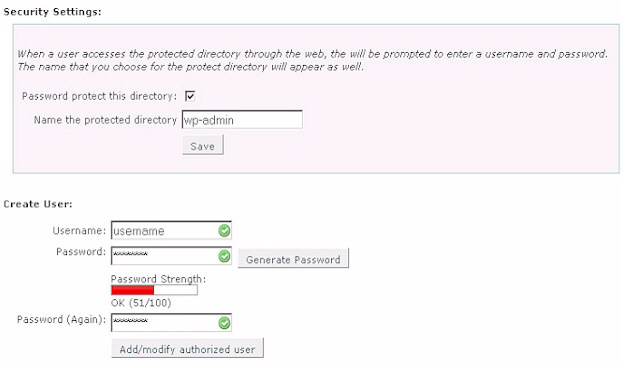
3. Password Protect the wp-admin Directory
htpasswd protect the wp-admin directory. This can usually be done through your web hosting control panel of your host’s file manager.
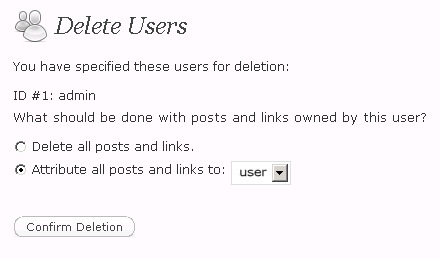
4. Delete the Admin User Account
When setting up WordPress, an administrator account with the user name admin is automatically created. Leaving the admin user account in place provides potential hackers half of the information they already need to access your blog. Only the password of this user would have to be cracked and they now have administrative access to your blog.
To alleviate this threat, create another administrator account with a different user name. Once you do this, log out and log back in with the new account at which time you can then delete the admin user account. Make sure that if you have created any posts and/or pages under the admin user account to attribute them to the new profile you have created or else they will be deleted at the same time you delete the admin account.
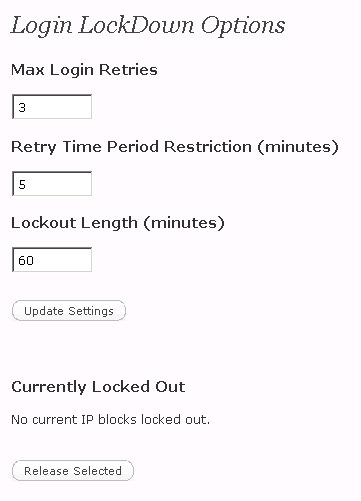
5. Restrict Erroneous Log-In Attempts
Unfortunately, WordPress does not record failed attempts to log in. This makes it next to impossible for the blog administrator to see an attack coming. Fortunately, there is a plug-in that solves this problem.
The Login LockDown plugin for WordPress will record all log-in attempts. Furthermore, it can lock out visitors for a specified time after a certain number of failed attempts.
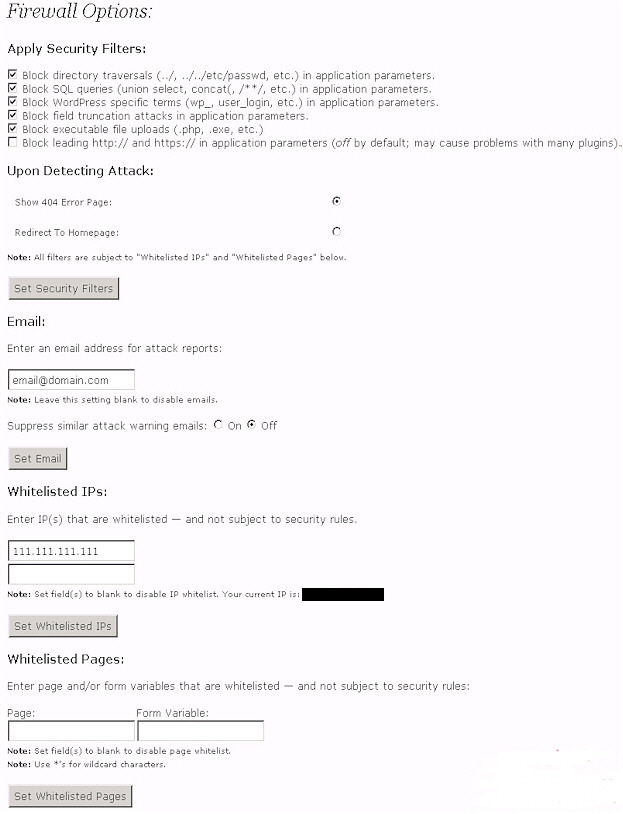
6. WordPress Firewall
This plugin investigates web requests with simple WordPress-specific heuristics to identify and stop most obvious attacks. A few powerful generic modules do exist that will accomplish the same task but they’re not always installed on web servers and if they are, can be difficult to configure.
WordPress Firewall intelligently whitelists and blacklists pathological-looking phrases based on which field they appear within in a page request (unknown/numeric parameters vs. known post bodies, comment bodies, etc.). Its purpose is not to replace prompt and responsible upgrading, but rather to mitigate 0-day attacks and let bloggers sleep better at night.
Features include —
- Detect, intercept, and log suspicious-looking parameters — and prevent them compromising WordPress.
- Protect most WordPress plugins from the same attacks.
- Respond with an innocuous-looking 404, or a home page redirect.
- Optionally send an email to you with a useful dump of information upon blocking a potential attack.
- Turn on or off directory traversal attack detection.
- Turn on or off SQL injection attack detection.
- Turn on or off WordPress-specific SQL injection attack detection.
- Turn on or off blocking executable file uploads.
- Turn on or off remote arbitrary code injection detection.
- Add whitelisted IPs.
- Add additional whitelisted pages and/or fields within such pages to allow above to get through when desirable.
If you have a static IP address or addresses by which you access your WordPress admin area, it is suggested that you add those IP addresses to the whitelist section of the plug-in’s settings.
7. WP Security Scan
This plug-in scans your WordPress installation for security vulnerabilities and suggests corrective actions.
For example, as long as the plug-in is activated, it will hide the version of WordPress you are using in the meta data information. This is important as it limits the information a potential hacker has in exploiting vulnerabilities of various versions of WordPress.
It also checks to make sure WordPress DB Errors are turned off and checks if an “admin” user account exists. The scanner function of the plug-in makes sure you have the correct permissions set on various files that can be exploited.
Finally, the plug-in contains a script that will allow you to change your database table prefix (wp_) to mitigate zero-day SQL Injection attacks.
Anything Else?
This is by no means an all-inclusive list. I’m sure there are additional steps that can be taken to manage and secure your WordPress blog from the hands of hackers. Please comment below if you would like to share additional methods or tools not mentioned here that are useful in protecting WordPress applications.









Hi David,
That’s a pretty good list.
You might want to be careful about number 3 though – there are quite a few hosts out there where this will cause a major error. Basically, after adding the password protection, the password prompt fails to come up and you get a 404 error instead.
I’m not sure how many people will be affected by this, but I was (on Hostgator) and there are quite a few people reporting the same thing on the Ask Apache Password Protect plugin (which does the same job as number 3 above) page.
For those who experience this problem, I have the solution at scratch99.com/2008/10/password-protecting-the-wp-admin-folder.
Most important (and obvious) one :
Use the lastest WordPress version.
Remove the WP version number that appears in the head of your HTML. This way potential hackers don’t know what version you are working with and thus unsure which exploits to try.
In the functions.php file of your theme add this line;
remove_action(‘wp_head’, ‘wp_generator’);
For me, I just update my wordpress blog to the lated release. I had wp blog have not been update since 2003, Hacker got it in no time, I had not format the server harddrive, reinstall server os, reinstall wp…